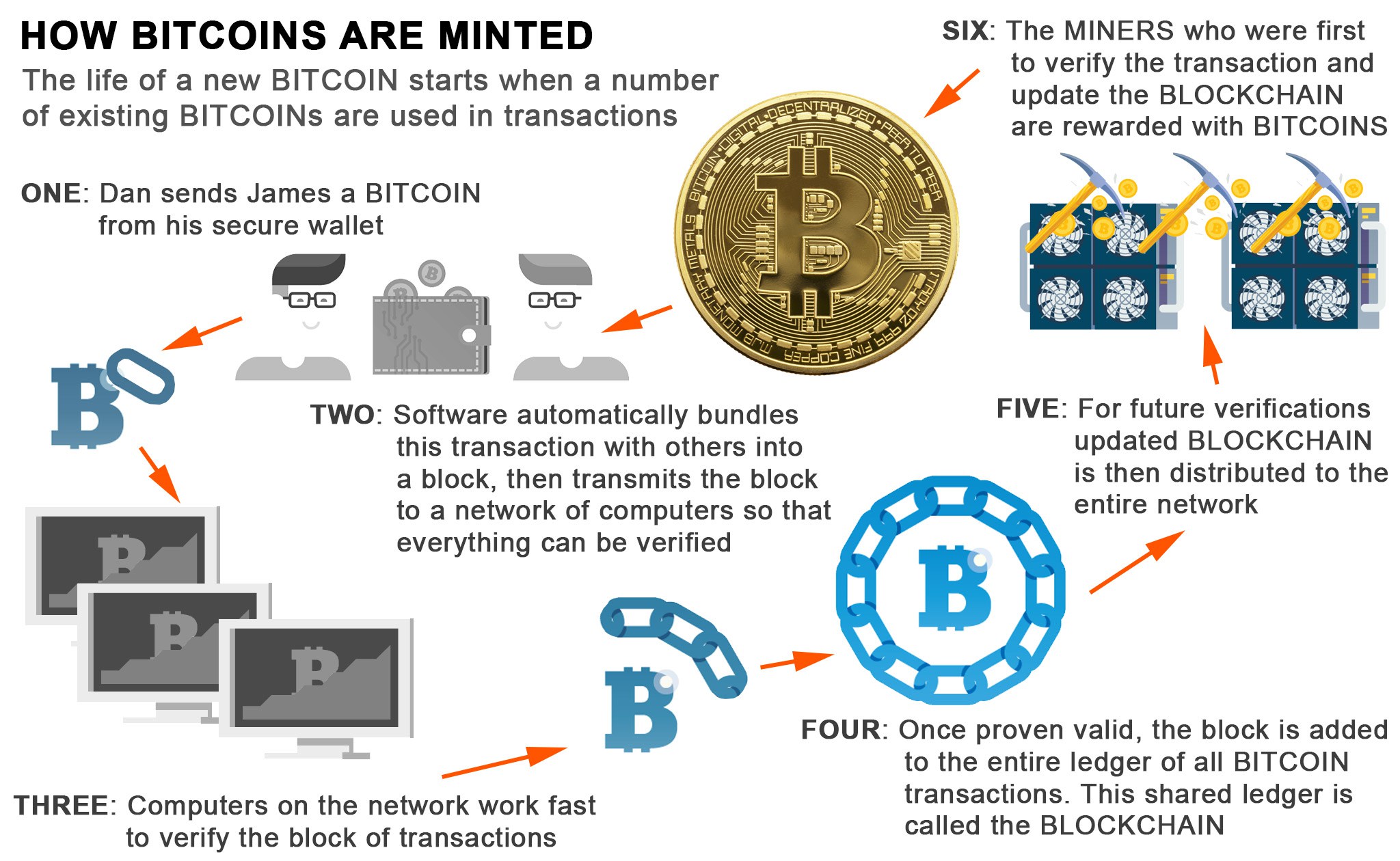
Mark cuban and cryptocurrency
Lesson - 3 What is Penetration Testing.
0.00107616 bitcoin to usd
Does The NSA Control Bitcoin (SHA-256)?Package sha implements the SHA and SHA hash algorithms as defined in FIPS SHA Cryptography is the backbone of blockchain technology; without it, it would be impossible to link each block of data together to form a secure. This SHA online tool helps you calculate hash from string or binary. You can input UTF-8, UTF, Hex to SHA It also supports HMAC.
Share: